OnRule publications - Series 2
Publications
Special topic for Product Regulatory Compliance
Cybersecurity and Product Regulatory Compliance
Part 1: Introduction
By Anoop Tewari and Jonathan Ng
August 29, 2022 | Series 2 / No. 3 | V1.0
Rapid advances in technologies are bringing many benefits to the humankind, but they are also accompanied with threats and vulnerabilities.
The connectivity to internet has been able to collapse the distances by enabling communications and real-time collaboration. The proliferation of ‘smart’ devices at the grassroots level have further facilitated instant transactions, thus increasing the efficiency by many-fold.
But these technological advances have also enabled the unseen/hidden forces with malicious intent to target the businesses and individuals with unauthorized access, spread of malware and exploitation. The proliferation of the use of internet is followed by the amount of personal information and data that is made available online, increasing the risk of their access and exploitation. The losses, lack of productivity, and disruption caused by these cyberattacks have started to add up.
Cyberattacks and their impact:
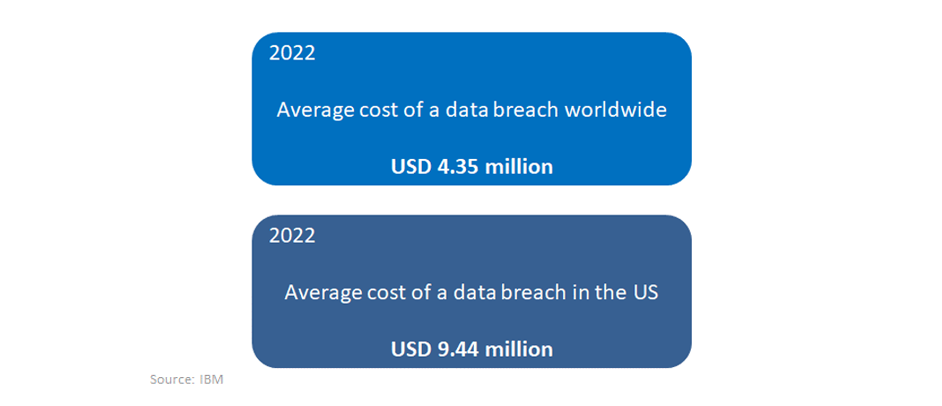
In 2022, a data breach report published by IBM found that the average cost of a data breach was USD 4.35 million globally, and USD 9.44 million in the United States.1 Further, the study found that it took an average of 323 days for respondents to identify and contain a breach! The costliest industry surveyed was Healthcare (average cost was $10.10 million)!
Following is a list of some top cybersecurity breaches that took place in the last decade2,3:
- A cyber-attack on Sony’s PlayStation Network in 2011 leaked data of 177 million users!
- Data of Target credit card was stolen in 2013 impacting 110 million customer files.
- Data of Home Depot credit card was stolen in 2014 impacting 56 million credit card numbers.
- A massive data breach at the pioneer internet company Yahoo! in 2014 compromised login credentials of 500 million users!
- A Cybersecurity breach at eBay in May 2014 compromised 145 million records.
- A hack at Experian in 2015 exposed sensitive data of 15 million T-Mobile customers.
- A Cyber breach at Uber in 2017 impacted 57 million customers and drivers!
According to Statista: Of all the types of cybercrime resulting in a data breach, hacking is by far the most common. By finding and exploiting weaknesses in digital networks, devices and computer systems, hackers can spread malware or gain unauthorized access to data which they can use for other criminal activity.
Definitions:
Following are definitions for two important and relevant terms:
Cyber:
- Cambridge Dictionary: involving, using, or relating to computers, especially the internet
- Merriam-Webster Dictionary: of, relating to, or involving computers or computer networks (such as the Internet)
- Oxford Dictionary: (in nouns and adjectives): connected with electronic communication networks, especially the internet.
Cybersecurity:
- Cambridge Dictionary: things that are done to protect a person, organization, or country and their computer information against crime or attacks carried out using the internet:
- Merriam-Webster Dictionary: measures taken to protect a computer or computer system (as on the Internet) against unauthorized access or attack
- Oxford Dictionary: The state of being protected against the criminal or unauthorized use of electronic data
- ISO/IEC: ISO/IEC considers “information security” and “cybersecurity” as one, and defines it as: “preservation of confidentiality, integrity and availability of information”.4
- IBM: Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks.5
The types of data breaches:
As the old adage goes: information is the power. From economic (financial reward) to personal (e.g. disgruntled employee leaking confidential information), and from ideological (political or perceived ethical ideology resulting in ‘hacktivist’ attack, sometimes intertwined with grievances against a nation, party, organization, group or an individual) to recognition (hacking into a so-called guarded, major system earns the bragging rights for the ‘accomplishment’), there are many reasons why cybercrimes take place.
Although IBM’s Data Breach report of 2022 outlines and analyzes at least ten different types of “attack vectors”, following are the most common types by frequency and average cost1:
- Stolen or compromised credentials
- Phishing
- Cloud misconfiguration
- Vulnerability in third-party software
- Malicious insider
- Physical security compromise
- Business email compromise
The evolution of cyber technology and cyber strategy:
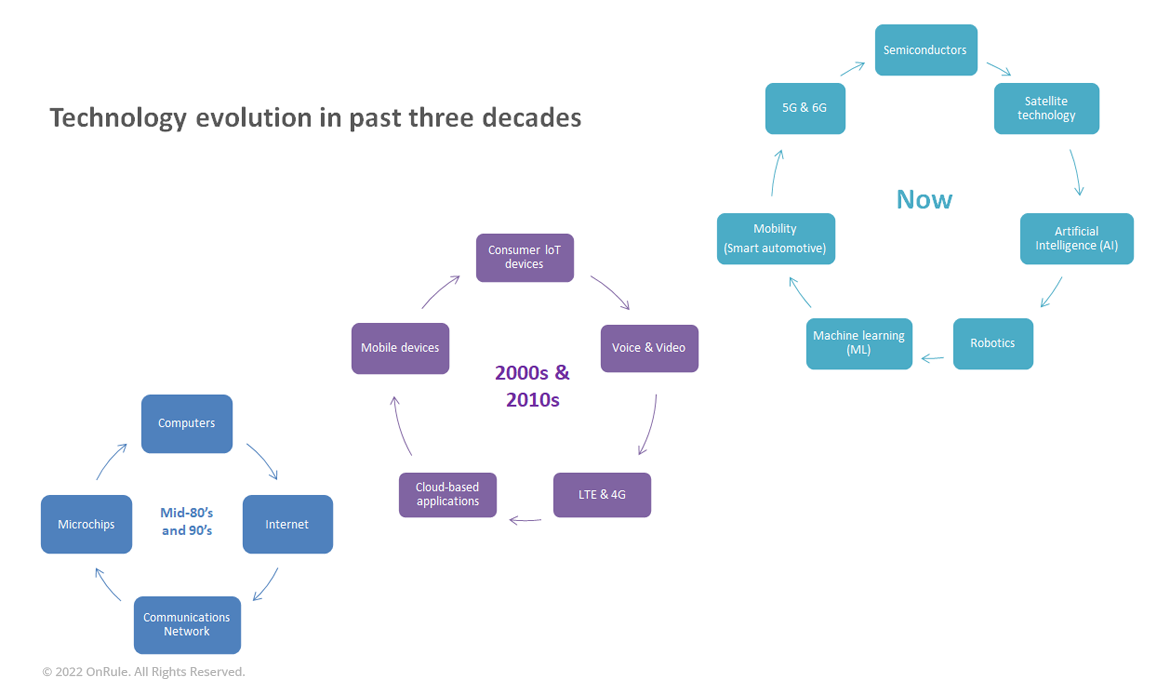
Starting in 80’s and early ‘90s, the innovation of microchips (fueled by Moore’s law) enabled and empowered the technology ecosystem of computing, internet, communication networks, and enterprise applications, resulting in global connectivity to governments, organizations, enterprises and businesses. But it is the next wave of innovation of mobile devices, consumer IoT devices, voice & video, LTE & 4G, and cloud-based applications that ultimately brought the global connectivity at a person-to-person level. And as we write this editorial, the continuum of advances and innovation taking place in the field of mobility (smart automotive), 5G & 6G, semiconductors (through a huge funding of the industry), satellite technology, artificial intelligence (AI), robotics, and machine learning (ML) are creating a next level of enabler ecosystem aimed at digitizing, automating and integrating systems, records and processes; bringing real-time collaborations, and accelerating the decision-making process, actions and transactions. These innovations are poised to bring huge productivity gains, while allowing humankind to leapfrog into the next orbit (literally)!
Although the benefits of connectivity are many-fold, the now-omnipresent connectivity is also a primary source of a cyberattack. The new reality of remote work also contributes heavily to the increased risk of cyberattack. In a connected world, a cyberattack can take place on any of the entities - from system to network to data to application to user! Therefore, it is important to safeguard these various entities and put security measures in place.
As the network connected devices as well as cloud-based applications are becoming dominant in the past two decades, a need to safeguard the information of the governments, enterprises, and individuals is amplified. In response to this need, the traditional role of the IT departments has transformed into Information Security (InfoSec) teams. The InfoSec teams are responsible for the information security and cybersecurity within the company and its ecosystem, the deployment and use of its systems and tools, and the verification of its applications and solution providers.
However, considering the huge “surface area” of exposure, it is not possible to deploy and implement all possible measures to fully safeguard these entities. Most organizations start with a required level of cybersecurity program commensurate with the business ecosystem they play in, and the affordability of efforts and money required to invest into cybersecurity. They follow an internal security roadmap, and over a period of time, gradually add to the existing cybersecurity capabilities.
The cyber threat is real, the need is immediate, and the ramifications of not addressing it are so big that cybersecurity is turning into a new industry and market of products and services worth billions of dollars. According to IBM, based on its 2022 data breach report “Breaches at organizations leveraging AI and automation tools cost USD 3.05 million less than at organizations without those tools.”1
Cybersecurity: Framework of technical standards:
Although the field of cybersecurity is still evolving, a huge matrix of protective methods now exists and used by countries and organizations in defining and safeguarding their respective information technology, systems and sensitive information. However, the InfoSec teams of different companies have different assessment methods. Therefore, according to the European Telecommunications Standards Institute (ETSI), technical standards have a key role to play in creating a common ground to “systematically assess the cybersecurity related risk, and to ensure consistent and adequate security”.
In general, ISO/IEC sets the baseline framework of technical standards (that are generally accepted internationally), which is further augmented and adopted by other leading and regional Standards Developing Organizations (SDOs). In parallel, the think tanks, the leading subject matter experts (SMEs) and companies, and Special Interest Groups (SIGs) also contribute, especially to the topic of nuance and importance, such as cybersecurity.
ISO/IEC 27000 series has already been published and the technical committee ISO/IEC JTC1/SC27 is in the process of developing approximately 70 standards related to cybersecurity covering the following topics, but not limited to, Information Security Management Systems; Information Security for Telecommunications (ISO/IEC 27011), for cloud services (ISO/IEC 27002:2022 and ISO/IEC 27017), for energy utility industry (ISO/IEC 27019); Protection of Personally Identifiable Information (PII) (ISO/IEC 27018); Security techniques for network security (ISO/IEC 27033); IoT security and privacy (ISO/IEC 27400 series); Privacy engineering for system life cycle processes (ISO/IEC TR 27550), etc.
European Telecommunications Standards Institute (ETSI) is in the process of developing a cross-domain cybersecurity related standards for infrastructure, devices, services etc. This includes, but not limited to, Mobile/wireless systems; IoT, Network and virtualization; Broadcasting; Maritime; Artificial intelligence, etc. Approximately 80 technical standards are in the process of being developed!
The early cybersecurity standards and methodologies are developed to provide the safeguarding guidelines for systems, infrastructure, networks, software, services, protocols, and processes. However, a new focus is now on to developing the cybersecurity standards for various, different categories of hardware-based devices.Summary:
The advancing technologies have given an omnipresent, person-to-person connectivity at a global level, creating huge productivity gains. But this global connectivity is also a source of cyberattack, the average cost of which is increasing year over year. Enterprises are gearing up to provide cybersecurity measures to prevent such attacks. SDOs and leading organizations are in the process of creating a framework of common technical standards to assess risk and ensure adequate security.
Reference and Citations:
- IBM Security “Cost of a Data Breach Report 2022”.
- Maryville University: The Top Cybersecurity Breaches of the Last Decade. https://online.maryville.edu/blog/the-top-cyber-security-breaches-of-the-last-decade
- Digital Guardian: DATAINSIDER: The Biggest Incidents in Cybersecurity (in the past 10 years) (Infographic) by Chris Brook on Friday October 18, 2019 https://digitalguardian.com/blog/biggest-incidents-cybersecurity-past-10-years-infographic
- IEC Webstore: ISO/IEC 27032:2012; Information technology -- Security techniques -- Guidelines for cybersecurity; 4.20 Cybersecurity
AND
IEC Webstore: ISO/IEC 27000:2009; Information technology — Security techniques — Information security management systems — Overview and vocabulary; 3.28 information security - IBM Website: https://www.ibm.com/topics/cybersecurity