OnRule publications - Series 2
Publications
Special topic for Product Regulatory Compliance
Cybersecurity and Product Regulatory Compliance
Part 2: Radio Equipment Directive and Article 3.3
By Anoop Tewari and Thomas Killam
September 28, 2022 | Series 2 / No. 4 | V1.0
The world of Product Regulatory Compliance covers many industries – from Information Technology Equipment (ITE) to Medical Electronics, from Appliance to Machinery, and from Toys to Unmanned Aircraft Systems!
According to the EU – "Today, wireless equipment is the target of more than 80% of cybersecurity attacks, compared to wired devices"1. Underscoring the importance of providing cybersecurity safeguards in a product, the European Union (EU) is bringing cybersecurity protection within the ambit of the product regulatory approval process. As part of this initiative, the EU is piloting its cybersecurity related regulations in its Radio Equipment Directive (RED) 2014/53/EU2 for certain categories of wireless devices.
Radio Equipment Directive and Article 3:
As shown in the following picture, the OEMs are familiar with and ensuring conformance of their products with radio to articles 3.1a (Health & Safety), 3.1b (Electromagnetic Compatibility), and 3.2 (Spectrum or Radio) of the Radio Equipment Directive.
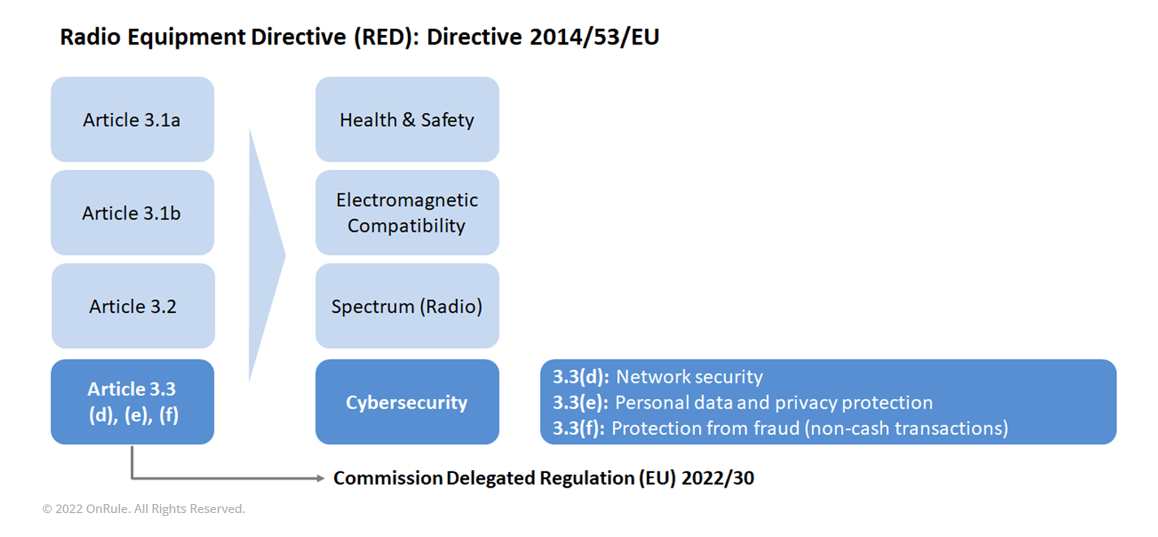
Now, emphasizing the importance of cybersecurity and to further strengthen it, the EU has adopted Commission Delegated Regulation (EU) 2022/303, which supplements the RED 2014/53/EU by activating articles 3.3(d), (e), and (f) of the RED.
This means that certain category of radio equipment will also have to meet the essential requirements of Article 3.3(d), (e), and (f) (in addition to the existing requirements of Article 3.1(a), (b), and 3.2). This additional requirement is aimed at increasing the level of cybersecurity by ensuring that the OEM has tested its radio equipment to prevent the hazards of cyber exposure and provided:
- the safeguards of the network within which it operates,
- the protection of personal data and privacy of the user and subscriber, and
- the protection from fraud.
Below is our understanding and explanation of these three articles, as well as few examples of safeguards that could be taken to conform to the articles and strengthen the cybersecurity:
- Article 3.3 (d): radio equipment does not harm the network or its functioning nor misuse network resources, thereby causing an unacceptable degradation of service
- A radio in a modern electronics equipment is typically an integrated circuit or a radio module. These radios get their operating characteristics, including power level gain of the radio transmitter, via commands that are sent to the radio chip or module through software configuration. The intent is to prevent a manipulation of these characteristics so that the radio will not disrupt normal radio communications from nearby equipment by saturating the radio spectrum.
- Set a hard limit on radio power to limit the range for short range radio devices. Use dip switches or other hardware-based limits that cannot be modified via software definition unless physical access to the equipment is provided.
- Set a hard limit on radio spectrum within which the equipment can operate. These may vary and be determined by the current deployment and intended use. The limits may be configured via dip switches or other hardware means that are tamper-proof and require physical access to the equipment.
- Internet-connected radio equipment could be compromised and taken hostage with malware, hacking, hacked software updates, etc. to become an agent in a network attack. A compromised node on a network could render the entire subnet and the devices in its immediate vicinity vulnerable.
The system must implement safeguards to protect itself from such attacks by having strong authentication systems. Implement a strong password policy: - Enforce minimum complexity requirements such as use of special characters, minimum length, use of numeric, etc. to avoid dictionary attacks.
- Support multi-factor-authentication (MFA)4. These methods use two or more different factors to achieve authentication. Factors include: (i) something you know (e.g., password/PIN); (ii) something you have (e.g., cryptographic identification device such as a YubiKey® or a token in the form of a private key); or (iii) something you are (e.g., biometric).
- Limit failed retry attempts to protect against brute force attack.
- Protect access with proper authentication and disallow default universal password.
- Allow use of third-party Single Sign-On (SSO) authentication service to allow users to maintain their desired level of security.
- If a system is compromised, equipment must have methods to detect the symptoms and notify the owner or administrator of such occurrence via monitoring agents, notification services and/or physical medium such as flashing lights:
- Detect and notify behavior such as sequential failures for authentication.
- Unusual volume of incoming/outgoing data traffic.
- High number of repeated application errors or network protocol errors.
- Equipment may implement methods to mitigate or diffuse the effects of such attacks if it detects that the system may have been compromised or an attack is in progress:
- Incorporate a bandwidth/packet limiter for incoming and outgoing data traffic to ensure the network is not flooded resulting in a denial of service.
- Implement timeout or lockdown of the equipment after an attack such as sequential authentication failures is detected.
- Article 3.3 (e): radio equipment incorporates safeguards to ensure that the personal data and privacy of the user and of the subscriber are protected
- Prior to gathering any PII, user is provided an option to opt-in or opt-out. Additionally, user is provided a clear explanation on how/why the PII data is being collected and its intended use:
- Provide user an option to opt-in or opt-out by asking user to click on an "I Agree" button prior to accessing the PII data.
- Handling of PII data requires enhanced protection:
- All PII data must always be encrypted at rest i.e., either stored locally on the equipment or in the cloud.
- When transmitted over network, all PII payload must be encrypted during transmission or the data must be transmitted on an encrypted channel e.g., Secure Socker Layer (SSL) or Transport Layer Security (TLS).
- User must be provided with an option to erase and completely remove the PII data when he or she chooses to do so:
- Allow a complete reset of system to its default state that includes secure removal of all user data.
- Camera’s activation could be compromised in the equipment such as a mobile device or laptop computer. In a compromised system, a camera could be turned on without the owner’s knowledge. Additionally, the system that provides visual indication of the camera’s operational state i.e., ‘Camera On’ or ‘Camera Off’ could be disabled. This could give bad actor an access to camera feed without the owner’s knowledge. Design considerations might include:
- Hardwire internally the ‘Camera On’ light to camera power. If the camera is turned on, the ‘Camera On’ light will turn on and cannot be independently disabled if the camera itself is on.
- Provide a physical/mechanical cover that can only be operated by having physical access to the equipment. This will allow the user to block the camera when it is not in use.
- Always-listening devices e.g., Amazon EchoTM, Google HomeTM, Siri® are always listening.
- Provide a physical/mechanical ‘Mute’ switch that can only be operated by having physical access to the device. The switch should disable the microphone in a fashion such that it cannot be enabled via built-in functionality or software. For example, muting the device using this switch would cut the power to the microphone.
- Article 3.3 (f): radio equipment supports certain features ensuring protection from fraud
- Always-listening devices e.g., Amazon EchoTM, Google HomeTM, Siri® are always listening.
- Providing personalization ability such as voice training of the owner and authorized users would limit the ability of unauthorized users to issue voice commands.
- Connected device may store authentication credentials or other cryptographical materials locally on the device. Securing the storage of this information is paramount to the security of the equipment:
- Store credential for wireless network in tamper-protected microcontroller rather than an external flash storage.
- Encrypt locally stored sensitive data.
- For devices that support cloud-based authentication or SSO service, all the communication related to authentication, and configuration change between the equipment and the cloud server must be on a secure channel:
- Encrypt the payload that contains sensitive information.
- Communicate over SSL/TLS type secure connection.
- Securing the supply chain is critical to protect the environment and therefore the equipment:
- Traceability strategies should be employed to ensure that all the field replaceable or repairable parts either software or hardware can be accounted for, and their origins can be authenticated and are traceable. This is required to ensure that the replaced or repaired components, post-deployment, have not been compromised at any stage of the supply chain.
- A robust software update process ensures longevity of equipment via feature enhancements, bug fixes, and updates deployed in response to vulnerabilities reported via Common Vulnerability Reporting Framework (CVRF)6 or other mediums:
- Ensure that the ecosystem that manages and delivers the software updates is itself protected and secured against cyber threats. A compromised system or distributor of updates could subvert one or many systems and equipment that it services.
- Implement secure boot mechanism on the equipment to protect deployment of any unauthorized updates that may be delivered inadvertently or from a compromised supply chain.
- Use of opensource software, opensource hardware, and third-party software is common practice. Ensuring integrity of such acquired hardware designs or software is critical to security of equipment:
- Opensource software if used, should only be acquired from a trusted source. Cybersecurity companies and organization offer support and services for the distribution of software. The software updates are verified and carry warranties of being malware free.
- Use integrity verification methods such as verifying the downloaded image checksums e.g., SHA2567 against the checksums provided by the trusted distributor.
- In-scope products1: The following is an example of products containing radio that are subjected to the legislation. Note that these are merely examples, and not all of them are explicitly listed in the legislation:
- Devices capable of communicating via the internet
- Consumer electronics: Smart phones, Tablets, Electronic cameras, Set-top box, etc.
- Internet of Things (IoT): Smart TV, Smart speaker, and Intelligent Assistant, also termed as ‘Always-listening devices’ (Amazon EchoTM, Google HomeTM, Apple Siri®, etc.); home automation devices such as door lock, thermostat, video camera, alarm; Smart sprinklers; robotic vacuum; Enterprise devices such as Smart lighting, Smart security, etc.
- Telecommunication equipment: Cellular modem, Cellular base station, etc.
- Information technology: Access point, Router, Printer, Laptops, Gateway, etc.
- Toys and childcare equipment
- Toys
- Baby monitors
- Wearables
- Smart watches
- Fitness trackers
- Jackets, blankets, or any wearable containing electronics such as heat warmers
- Exempt products1: This legislation is not applicable to the following product categories because their cybersecurity is guaranteed by existing pieces of dedicated legislation under which they are already covered:
- Motor vehicles
- Electronic road toll systems
- Equipment to control unmanned aircraft remotely
- Non-airborne specific radio equipment that may be installed on aircrafts
- Medical devices
- In-vitro medical devices
Connected devices with radio must coexist on the network and operate in a fashion such that they do not degrade or disrupt the operation of the network to which they are connected. The equipment shall participate in making networks more resilient. The equipment shall incorporate features to avoid misuse or harm to the communication networks.
Transmitter power level on the radio of the equipment could be manipulated to cause jamming of radio spectrum it operates in. An equipment could introduce a powerful Radio frequency (RF) signal to overwhelm the spectrum being used by the system, thus denying service to all wireless nodes within the range of the interference.
For equipment that allows software defined configuration e.g., software defined radio (SDR) or software defined network (SDN), the Equipment design should include safeguards to prevent unintended redefinition of the system via software upgrades. Redefinition of the equipment by changing deployed software/firmware could result in modifying the equipment’s capabilities beyond what may be permissible for the current installation e.g., change the radio power or operating frequency spectrum. Therefore, the equipment should have ability to enforce hard limit that can avoid such intended or unintended violations:
Regulation (EU) 2016/679 of the European Parliament5, which is a new General Data Protection Regulation (GDPR), declares that "The protection of natural persons in relation to the processing of personal data is a fundamental right". It declares the right to the privacy and protection of personal data and Personally Identifiable Information (PII).
Improve the handling and protection of personal data and consumers’ privacy. Devices that can access information that constitutes PII must take care of abiding by the rules of collecting, storing, and using this data. Safeguards must be implemented to protect personal data and consumers’ privacy.
While there may be commitment by the manufacturer to limit the amount of recording the equipment will retain, a threat actor could get access to private conversation and abuse the information gathered from the recording. The device should give user the option to stop any listening or recording:
Reduce the risk of monetary fraud. Financial fraud can occur if a perpetrator gains unauthorized access to equipment. The protection of equipment from unauthorized access would require securing not only the equipment itself, but its ecosystem in which it operates, and its manufacturing supply chain.
Each equipment depending on the nature of the product, i.e., all hardware platform, hardware-software, or software defined hardware, will have to employ strategies to harden the security and prevent fraud.
These devices are also capable of managing smart devices such as thermostat, electrical switches, door locks, and many others. A bad actor could operate other smart devices if they could get proximity access. Design consideration might include the implementation of voiceprint authentication:
A defense-in-depth strategy is necessary to protect an equipment and ensure that it cannot be subverted by protecting it via robust design as well as safeguarding the ecosystem that it is part of.
Scope of Article 3.3:
Timeline relevance:
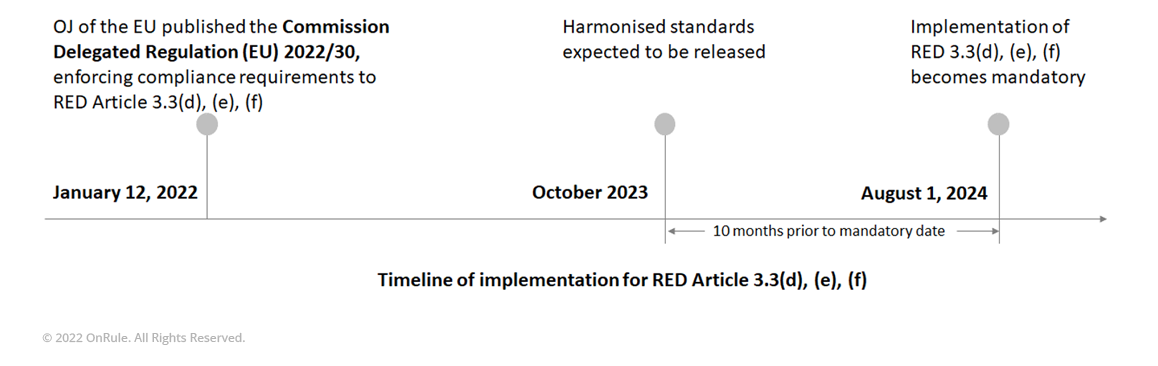
The Official Journal (OJ) of the EU published the delegated regulation on January 12, 2022. The implementation of this becomes mandatory on August 1st, 2024. However, the harmonized standard in support of this legislation is intended to be made available ten months before the mandate, which is by October 2023.
How will manufacturers comply to this new piece of legislation?
Although the mandatory date for this new piece of legislation is not going into effect until August 1st, 2024, there are many forward-looking manufacturers that would like to start complying now for a couple of reasons: one, an early start gives a competitive advantage; and two, when one is complying proactively, it is one’s opportunity to learn and be prepared with all the requirements and documentation when the mandate kicks in.
Today, the EU does not have a harmonized standard available in support of this legislation. However, the European Standardization Organizations (ESO) have been instructed to develop the harmonized standard. It is expected that the harmonized standard(s) will be made available 10 months before the mandate, which means, it will be made available in October 2023.
In the meantime, today, in the absence of a harmonized standard, a manufacturer may take any of the following routes in performing the conformity assessment on its product:
- Presumption of conformity: Identify any technical methods to demonstrate the presumption of conformity to the essential requirements. In the absence of a harmonized standard, a manufacturer can use from the list of many available Cybersecurity standards related to its product category. In Part 1,8 of this editorial we have provided a list of organizations that have developed and are in the process of further developing cybersecurity related standards. For example,
- For Consumer Internet of Things (IoT) devices, a manufacturer may refer to ETSI EN 303 645 V2.1.1 (2020-06)9 to find the baseline requirements, and outcome-focused provisions.
A manufacturer may also refer to ETSI TS 103 701 V1.1.1 (2021-08)10 to find the relevant test cases for baseline conformance assessment against the EN. - For industrial automation and control systems (IACS), which are not part of the Cybersecurity requirements of the RED today, a manufacturer may refer to IEC-62443-2-411 for a comprehensive set of requirements for security capabilities for IACS service providers.
- The manufacturer may also reference a proprietary standard or procedure. To better understand various aspects of security validation for Web of Things (WoT), refer to Section 8 of the article "Web of Things (WoT) Security and Privacy Guidelines"12
- Conformity assessment: The following are the available options to assess the conformity:
- If the technical method is using a harmonized standard, the manufacturer can self-declare without the need to get a Notified Body involved.
- If the technical method is not using a harmonized standard, the manufacturer must take either of the following two approaches.13
- Notified body: Since the harmonized standard is not yet made available to support Article 3.3, all presumption of conformity must involve a Notified body. A manufacturer may employ a third-party Notified Body (NB) to obtain an EU-Type Examination Certificate based on the internal production control. This is explained in Article 17 and Annex III of the RED.
- Quality assurance system: Conformity based on full Quality assurance system as detailed in Annex IV of the RED
- Documentation: Create a Declaration of Conformity (DoC), identify the Notified body, if involved, and include the Type Examination Certificate. The manufacturer can also cite the technical documents, procedures, and standards (proprietary or otherwise) used from 1 above, to demonstrate the presumption of conformity.
For practical purposes, in the beginning, we foresee most of the organizations using the Notified body to assess the conformity on a per-product basis.
Summary:
Underscoring the urgency required in tackling the cyber threat, the EU has enhanced the existing RED, mandating conformance to the Cybersecurity requirements for the in-scope products. But considering the complexity of Cybersecurity, developing and recommending the underlying technical standards as means to presumption of conformity is a challenge. The EU has assigned the European Standards Developing Organization (SDO) to develop the underlying technical standards in support of this new legislation, which are targeted to be released by October 2023.
Reference and Citations:
- Commission, E. (2021, October 29). Questions and Answers: Strengthening cybersecurity of wireless devices and products. European Commission. Retrieved July 7, 2022, from https://ec.europa.eu/commission/presscorner/detail/en/QANDA_21_5635
- DIRECTIVE 2014/53/EU OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL. An official website of the European Union. (2014, April 16). Retrieved July 10, 2022, from 111
- Commission, E. (2021, October 29). Lex - 32022R0030 - en - EUR-lex. EUR. Retrieved July 11, 2022, fromhttp://data.europa.eu/eli/reg_del/2022/30/oj
- Paulsen, C., & Byers, R. (2019, July). Computer Security Resource Center. CSRC. Retrieved July 20, 2022, fromhttps://csrc.nist.gov/glossary/term/multi_factor_authentication
- Union, C. of the E., & Parliament, E. (2016, April 27). Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 april 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and Repealing Directive 95/46/EC (General Data Protection Regulation) (text with EEA Relevance). Photo of Publications Office of the European Union. Retrieved July 21, 2022, from https://op.europa.eu/en/publication-detail/-/publication/3e485e15-11bd-11e6-ba9a-01aa75ed71a1
- Hagen, S. (Ed.). (2017, September 13). CSAF Common Vulnerability Reporting Framework (CVRF) Version 1.2. Retrieved July 22, 2022, from http://docs.oasis-open.org/csaf/csaf-cvrf/v1.2/csaf-cvrf-v1.2.html
- Eastlake, D., & Hansen, T. (2011, May). RFC 6234 - US secure hash algorithms (sha and SHA-based HMAC and HKDF). US Secure Hash Algorithms. Retrieved July 22, 2022, from https://datatracker.ietf.org/doc/html/rfc6234
- Tewari, A., & Ng, J. (2022). Cybersecurity and Product Regulatory Compliance; Part 1: Introduction. OnRule. Retrieved July 26, 2022, from https://onrule.com/resources/product-regulatory-compliance-cybersecurity.html
- ETSI - Welcome to the world of standards! ETSI. (2020, June). Retrieved July 11, 2022, from https://www.etsi.org/deliver/etsi_en/303600_303699/303645/02.01.01_60/en_303645v020101p.pdf
- ETSI - Welcome to the world of standards! ETSI. (2021, August). Retrieved July 11, 2022, from https://www.etsi.org/deliver/etsi_ts/103700_103799/103701/01.01.01_60/ts_103701v010101p.pdf
- Technical Committee, I. E. C. (Ed.). (2017). Webstore international electrotechnical commission. Welcome to the IEC Webstore. Retrieved July 22, 2022, from https://webstore.iec.ch/publication/61335
- Reshetova, E., & McCool, M. (Eds.). (2019, November). Web of things (WOT) security and privacy guidelines. W3C. Retrieved July 12, 2022, from https://www.w3.org/TR/wot-security/
- Radio Equipment Directive (RED), Article 17: Conformity assessment procedures; 3 & 4: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:32014L0053